Mandatory MFA for Azure Access
as of July 2024
This July, Azure teams will begin rolling out additional tenant-level security measures to require multi-factor authentication (MFA). Establishing this security baseline at the tenant level puts in place additional security to protect your cloud investments and company.
The roll-out of this requirement will be gradual and methodical to minimize impact on your use cases.

How does MFA work?
Multi-factor authentication (MFA) is a security method that requires users to provide two or more pieces of evidence to verify their identity before accessing a service or a resource. The evidence can be something the user knows (such as a password or a PIN), something the user has (such as a phone or a token), or something the user is (such as a fingerprint or a face scan).
MFA adds an extra layer of protection to the standard username and password authentication, making it harder for attackers to compromise accounts and steal data. MFA can also help prevent unauthorized access due to phishing, credential stuffing, brute force, or password reuse attacks.
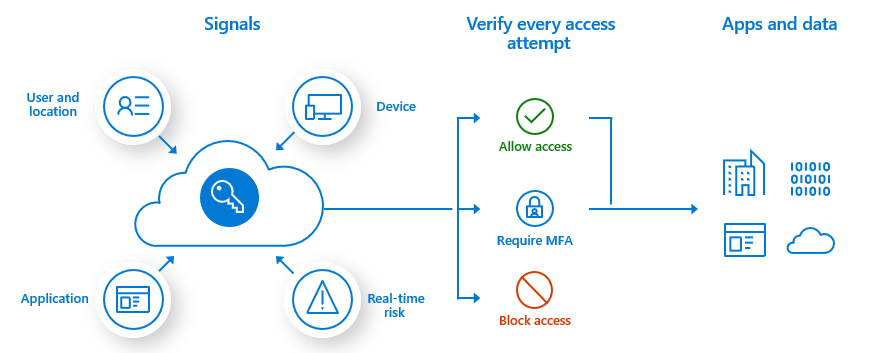
Entra ID supports various MFA methods, such as Microsoft Authenticator app, SMS, voice call, and hardware tokens. Users can choose the method that suits their preferences and needs. Admins can also use Entra ID Conditional Access policies to tune when MFA is required based on signals such as the user’s location, device, role, or risk level.
Why is MFA important for Azure tenant security?
The need for MFA is more important than ever, as cyberattacks are becoming more frequent, sophisticated, and damaging. According to a report by Microsoft, 99.9% of compromised accounts did not use MFA. The report also found that MFA can block more than 99.2% of account compromise attacks, making it one of the most effective security measures available.
The rise of the hybrid workforce and accelerated digital transformation of businesses by the COVID-19 pandemic expanded risk scenarios for employees and companies. Today, more people work outside of the office and access data and applications from various devices and locations. All of this has increased the attack surface and the potential for unauthorized access, as users may use unsecured networks, devices, or passwords. MFA can help mitigate these risks by adding an extra verification step and preventing access from unknown or suspicious sources.
MFA is also a key component of identity and access management, which involves ensuring that only authorized and authenticated users can access the services and resources. One of the three areas of engineering advancements within Microsoft’s Secure Future Initiative focuses on implementing new identity protections and MFA at the tenant level helps you with identity protections. MFA not only reduces the risk of account compromise and data breach, but it also helps you comply with various security standards and regulations, such as PCI DSS, HIPAA, GDPR, and NIST.


For whom is this important?
This means that users will need to provide a second factor of authentication, such as a code from an authenticator app, a text message, a phone call, or a security key, in addition to their password, whenever they sign in to Azure.
This policy will apply to all Azure users, regardless of their subscription type, role, or location.
MFA will be mandatory for physical users when accessing Azure through:
- Azure portal.
- Azure CLI.
- Azure PowerShell.
- Third party Azure tools like Terraform or Ansible.
This new policy has no impact on:
- Users who consume apps, websites or services deployed on top of Azure.
- Azure managed identities and service principals.
This policy will not affect users who access other Microsoft services, such as Office 365, OneDrive, or Outlook, unless they are also Azure users or their organizations have enabled MFA for those services as well.
Already deployed conditional access policies?
This new policy is cumulative to your own CA policies. Microsoft will opt for the most restrictive policy and apply it to the authentication process.
What about break the glass accounts?
Partners or customers who have setup break the glass accounts with “a very long password stored in a vault” will need to setup another authentication method for this account. We advise you to make use of a hardware token and store this in the vault.
What MFA solutions are accepted?
Nothing changes. These are the available verification methods: Microsoft Authenticator, Windows Hello for Business, FIDO2 security key, OATH hardware token (preview), OATH software token, SMS, voice call.
What about users from other tenants?
Users from outside of the tenant (guest, federated, etc.) who have already logged into their own tenant using MFA / strong authentication, are exempt of this policy and will not have to respond to a second MFA challenge.
I use a physical user account to run automation on Azure.
Don’t. Please update and use a service principal or managed identity.

Don’t miss this opportunity to enhance your expertise in Azure Arc for SQL. We encourage you to share this invitation with colleagues who would also benefit from these sessions.
Don’t hesitate to contact us for more questions: microsoft.be@tdsynnex.com
The Microsoft team at TD SYNNEX